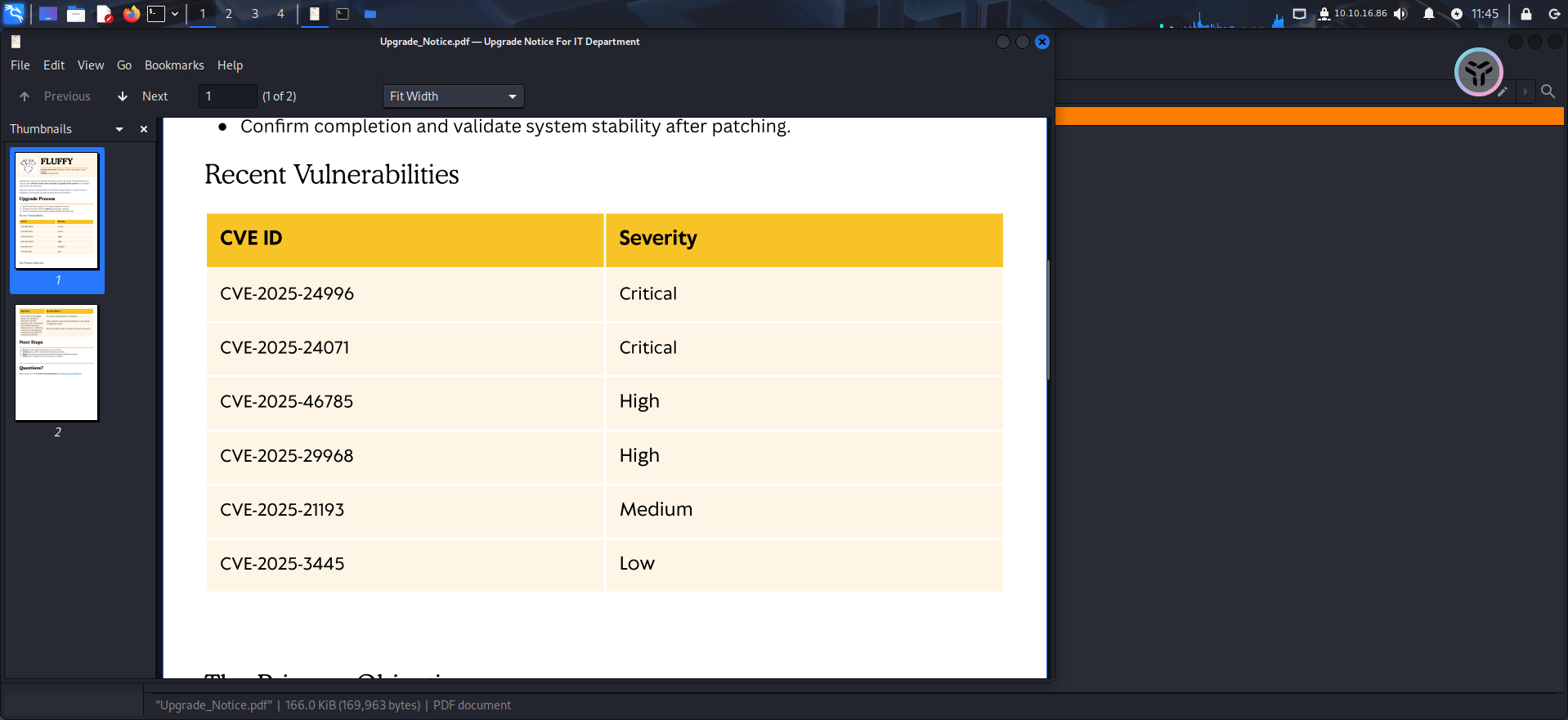
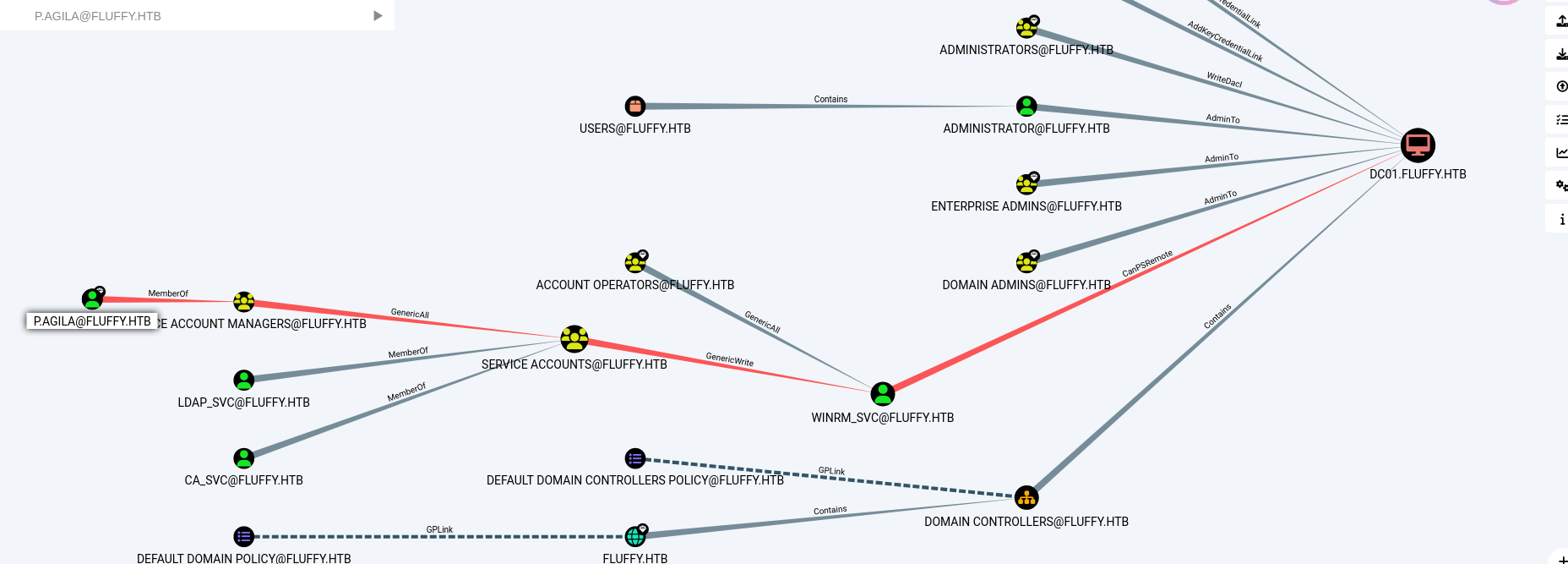
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
| ┌──(root㉿kali)-[~/Desktop/tmp]
└─# rustscan -a 10.10.11.69 -- -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
____ ____ ____ ____ ____ ____ ____ ____ ____ ____
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we're dating.
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 65435'.
Open 10.10.11.69:53
Open 10.10.11.69:88
Open 10.10.11.69:139
Open 10.10.11.69:389
Open 10.10.11.69:445
Open 10.10.11.69:464
Open 10.10.11.69:593
Open 10.10.11.69:636
Open 10.10.11.69:3268
Open 10.10.11.69:3269
Open 10.10.11.69:5985
Open 10.10.11.69:9389
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} -{{ipversion}} {{ip}} -sV" on ip 10.10.11.69
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-04 11:37 EDT
NSE: Loaded 47 scripts for scanning.
Initiating Ping Scan at 11:37
Scanning 10.10.11.69 [4 ports]
Completed Ping Scan at 11:38, 2.83s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:38
Completed Parallel DNS resolution of 1 host. at 11:38, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 11:38
Scanning 10.10.11.69 [12 ports]
Discovered open port 53/tcp on 10.10.11.69
Discovered open port 5985/tcp on 10.10.11.69
Discovered open port 445/tcp on 10.10.11.69
Discovered open port 139/tcp on 10.10.11.69
Discovered open port 9389/tcp on 10.10.11.69
Discovered open port 389/tcp on 10.10.11.69
Discovered open port 464/tcp on 10.10.11.69
Discovered open port 636/tcp on 10.10.11.69
Discovered open port 88/tcp on 10.10.11.69
Discovered open port 3269/tcp on 10.10.11.69
Discovered open port 3268/tcp on 10.10.11.69
Discovered open port 593/tcp on 10.10.11.69
Completed SYN Stealth Scan at 11:38, 0.36s elapsed (12 total ports)
Initiating Service scan at 11:38
Scanning 12 services on 10.10.11.69
Completed Service scan at 11:38, 48.89s elapsed (12 services on 1 host)
NSE: Script scanning 10.10.11.69.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:38
Completed NSE at 11:38, 0.87s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:38
Completed NSE at 11:38, 1.09s elapsed
Nmap scan report for 10.10.11.69
Host is up, received echo-reply ttl 127 (0.74s latency).
Scanned at 2025-06-04 11:38:01 EDT for 51s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-06-04 22:16:38Z)
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o: microsoft: windows
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.35 seconds
Raw packets sent: 20 (832B) | Rcvd: 19 (868B)
|